ESET research
ESET researchers discovered a zero-day Telegram for Android exploit that can send malicious files disguised as videos
July 22, 2024
•
,
6 min read

ESET researchers discovered a zero-day exploit targeting Telegram for Android, which appeared for sale for an unspecified price starting June 6 in an underground forum poste2024. Using the exploit to exploit a vulnerability we dubbed EvilVideo, attackers were able to share malicious Android payloads across Telegram channels, groups, and chat, and make them appear as multimedia files.
We found an example of the exploit, which allowed us to analyze it further and report it to Telegram on June 26.e2024. On July 11ethey have released an update that fixes the vulnerability in Telegram versions 10.14.5 and higher.
Figure 1 is a video demonstration and explanation of the EvilVideo vulnerability.
Figure 1. Explanation of the EvilVideo vulnerability
Key points of the blog post:
- On June 26eIn 2024, we found an advertisement for a zero-day exploit targeting Telegram for Android on an underground forum.
- We named the exploited vulnerability EvilVideo and reported it to Telegram; their team patched it on July 11the2024.
- EvilVideo allows attackers to send malicious payloads that appear as video files in the unpatched Telegram for Android.
- The exploit only works on Android Telegram versions 10.14.4 and older.
Discovery
We discovered that the exploit was offered for sale on an underground forum: see Figure 2.
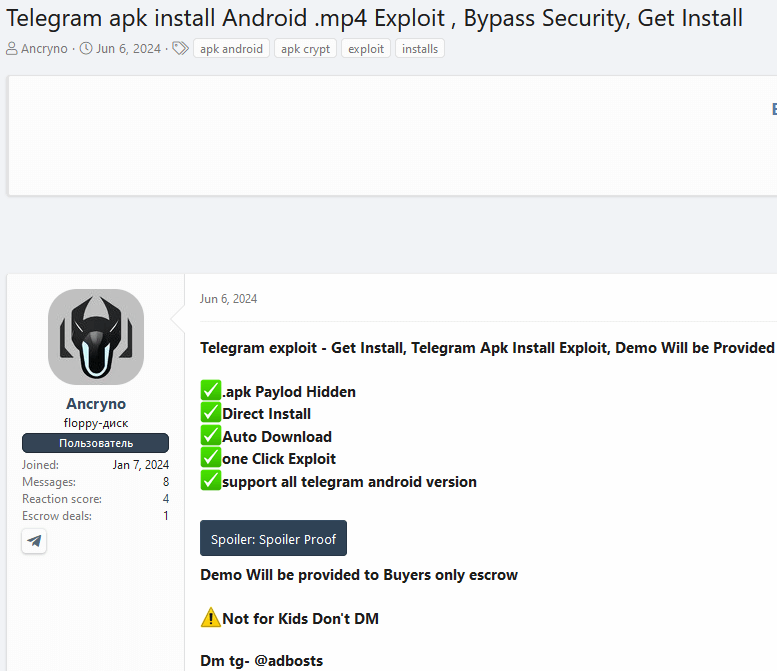
In the post, the seller shows screenshots and a video of testing the exploit on a public Telegram channel. We were able to identify the channel in question, while the exploit is still available. This allowed us to get our hands on the cargo and test it ourselves.
Analysis
Our analysis of the exploit showed that it works on Telegram versions 10.14.4 and older. We speculate that the specific payload was most likely created using the Telegram API, as it allows developers to programmatically upload specifically crafted multimedia files to Telegram chats or channels.
The exploit appears to rely on the threat actor being able to create a payload that displays an Android app as a multimedia preview and not as a binary attachment. Once shared in chat, the malicious payload appears as a 30-second video (Figure 3).
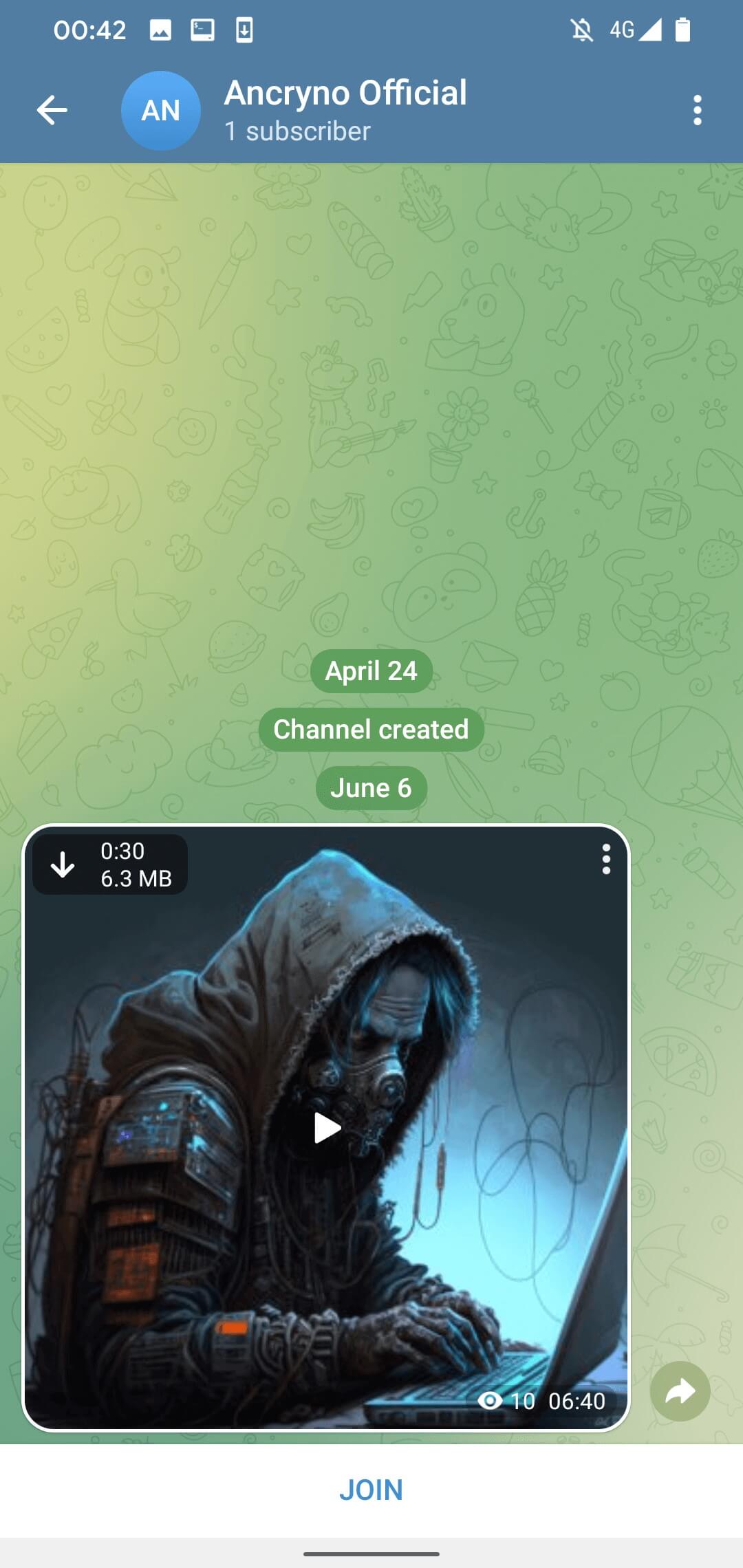
By default, media files received via Telegram are set to download automatically. This means that users with the option enabled will automatically download the malicious payload as soon as they open the conversation where it was shared. The option can be manually disabled – in which case the payload can still be downloaded by tapping the download button in the top left corner of the shared, visible video, as visible in Figure 3.
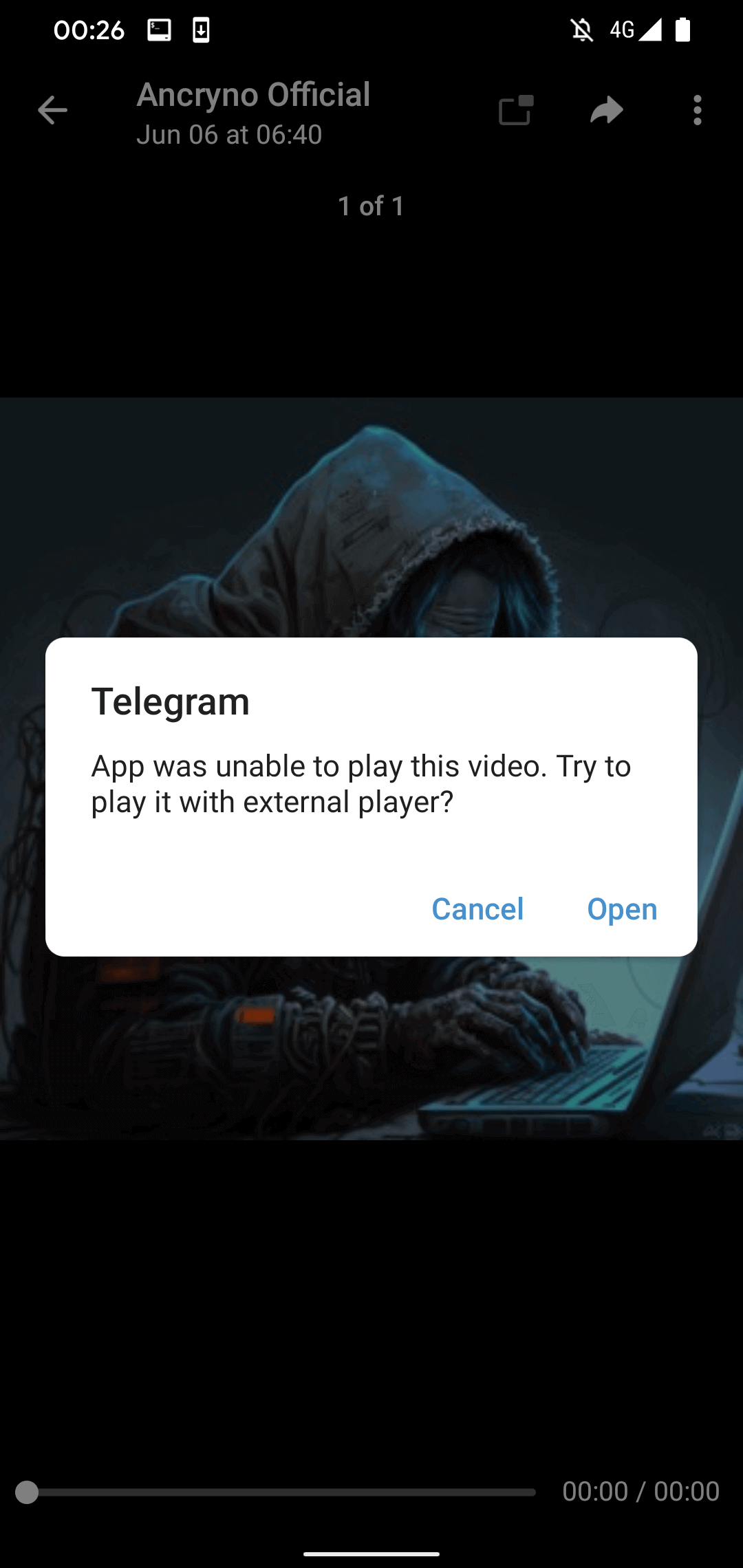
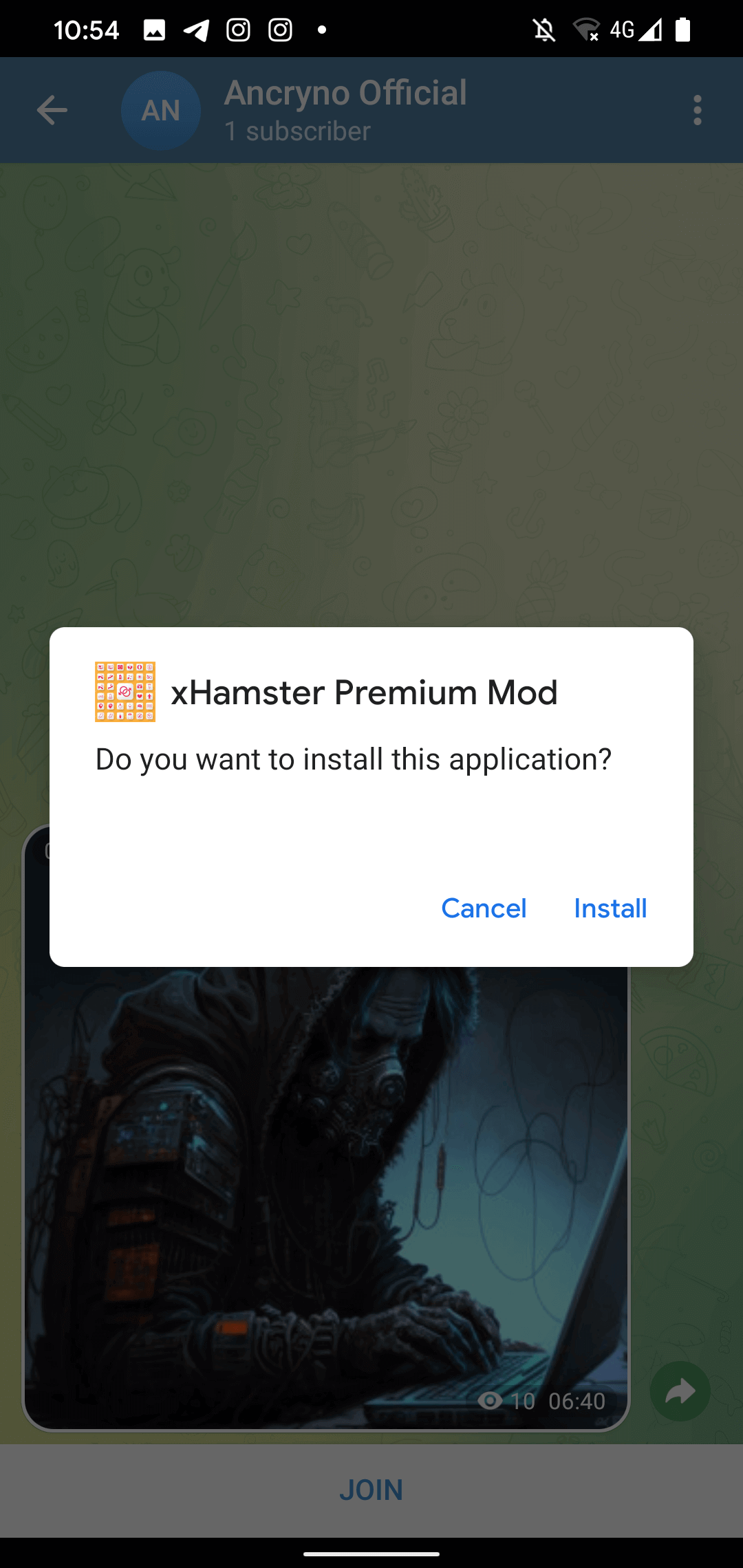
If the user tries to play the “video”, Telegram displays a message saying it cannot be played and suggests using an external player (see Figure 4). This is an original Telegram warning that we found in the source code of the legitimate Telegram for Android app; it was not created and pushed by the evil payload.
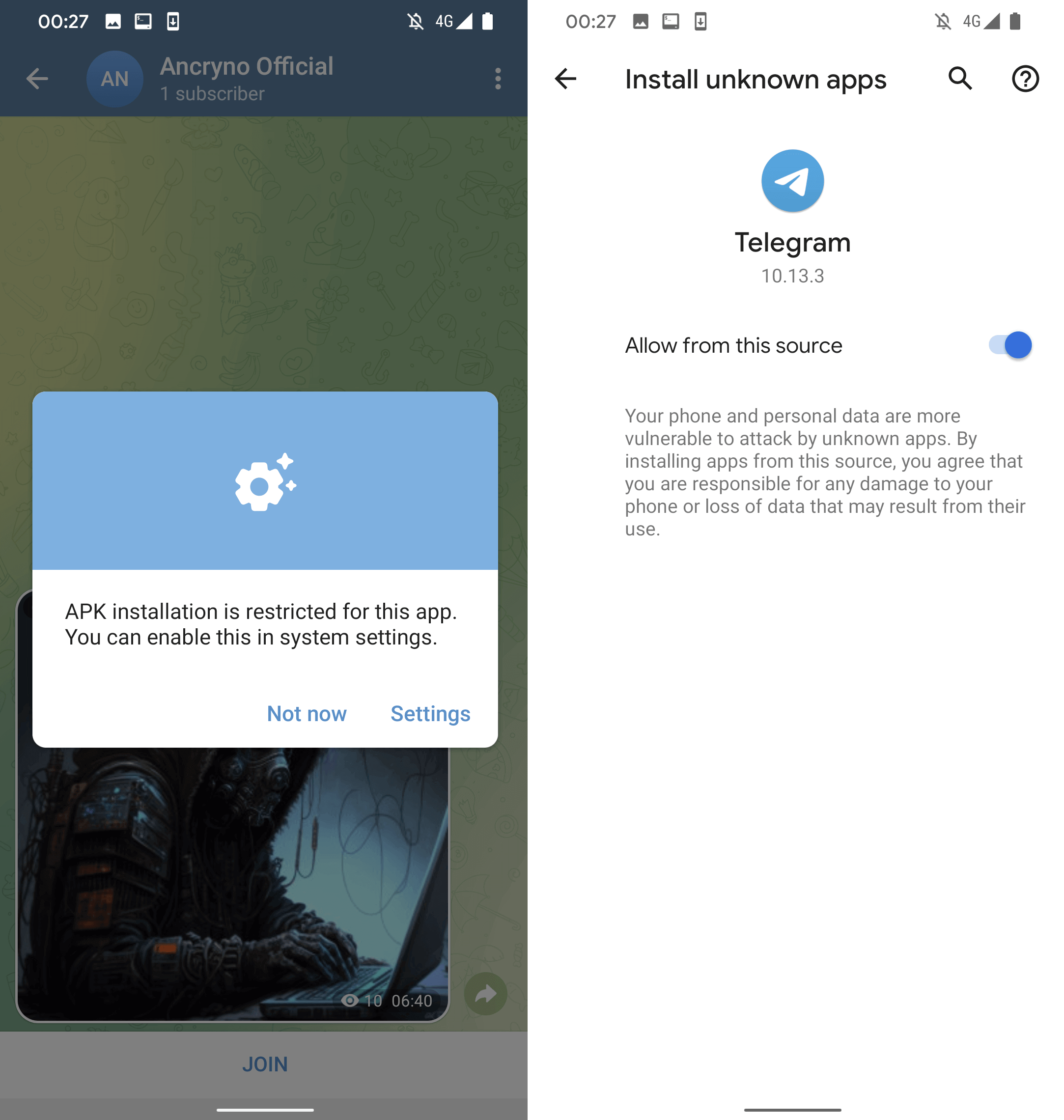
However, if the user taps the Open button on the displayed message, they will be prompted to install a malicious app disguised as the aforementioned third party player. As shown in Figure 5, before installation, Telegram will ask the user to enable installation of unknown apps.
At this point, the malicious app in question has already been downloaded as the apparent video file, but with the .apk extension. Interestingly, it is the nature of the vulnerability that makes the shared file look like a video: the actual malicious app has not been modified to masquerade as a multimedia file, indicating that the upload process has most likely been exploited. The installation request of the malicious app can be seen in Figure 6.
Unfortunately, we were unable to replicate the exploit. We only inspected and verified the sample shared by the seller.
Telegram web and desktop
Although the payload was intended solely to target Telegram for Android, we still tried to test its behavior on other Telegram clients. We tested both the Telegram Web client and the Telegram Desktop client for Windows. As expected, the exploit didn’t work on either.
In the case of Telegram Web, after we tried to play the “video,” the customer displayed an error message telling us to try opening the video with the desktop app (see Figure 7). Manually downloading the attached file revealed its name and extension Teating.mp4. Although the file itself was actually an Android executable binary (APK), Telegram prevented the exploit from working: to be successful, the attachment had to have the following characteristics: .apk extension.
Something similar happened with the Telegram Desktop client for Windows: the downloaded file was given a name Teating.apk.mp4so it was again a binary APK file with a .mp4 extension. This suggests that even if an attacker were to create a Windows executable to use instead of the Android APK, it would still be treated as a multimedia file and the exploit would not work.

Threat actor
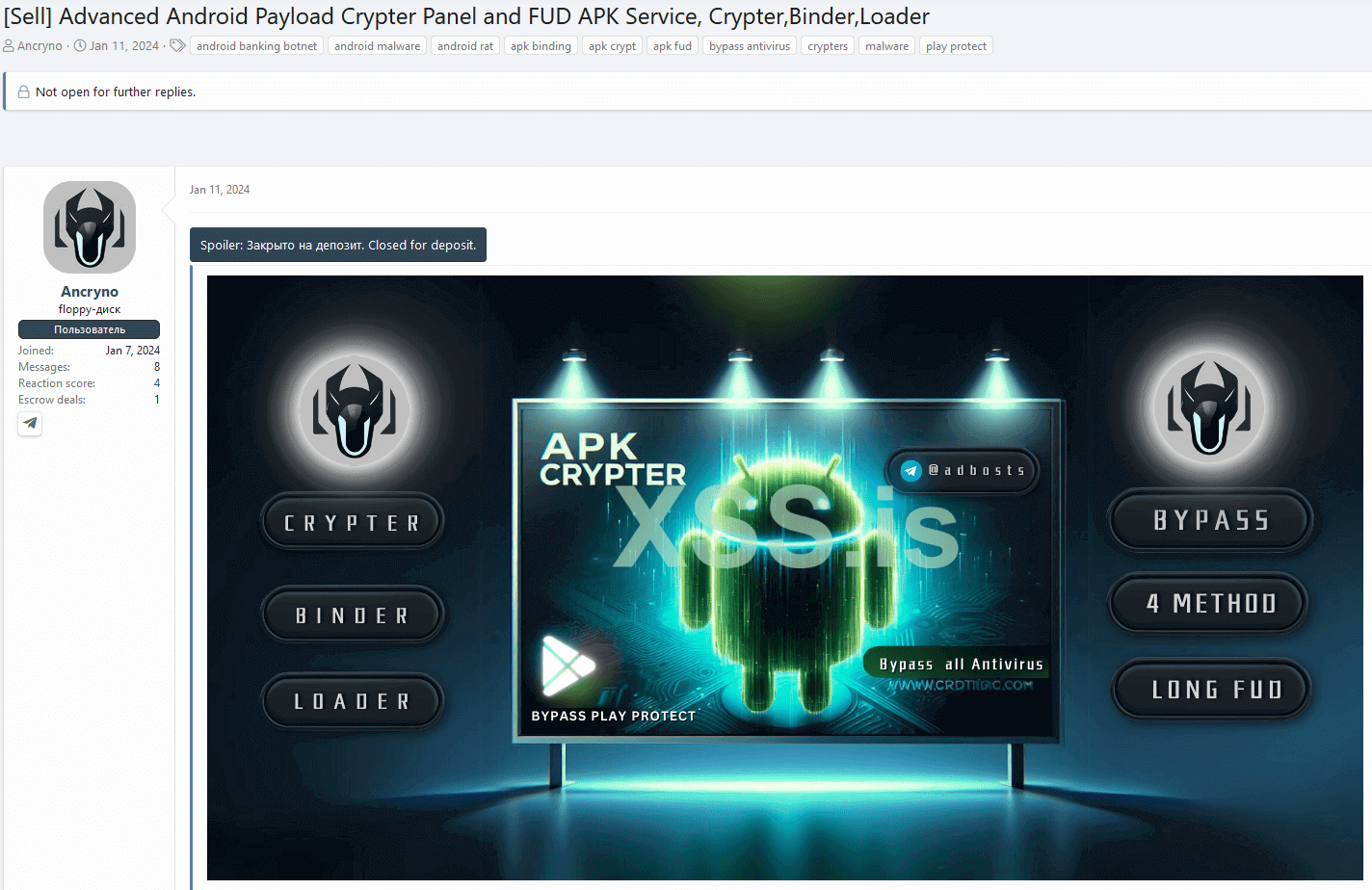
While we don’t know much about the threat actor, we managed to find another shady service they offer, based on the Telegram handling that the seller shared in his forum post. In addition to the exploit, they have been using the same underground forum since January 11 to advertise an Android cryptor-as-a-service that they claim is completely undetectable (FUD).e2024. The forum post can be seen in Figure 8.
Vulnerability report
After discovering the EvilVideo vulnerability on June 26e2024, we followed our coordinated disclosure policy and reported it to Telegram, but received no response at the time. We reported the vulnerability again on July 4e, and that time Telegram contacted us the same day to confirm that its team was investigating EvilVideo. They fixed the issue and shipped version 10.14.5 on July 11eand informed us via email.
The vulnerability affected all versions of Telegram for Android up to and including 10.14.4, but was patched starting with version 10.14.5. As we verified, the chat multimedia preview now correctly shows that the shared file is an application (Figure 9) and not a video.

Conclusion
We discovered a zero-day Telegram for Android exploit for sale on an underground forum. The vulnerability it exploits allows malicious payloads resembling multimedia files to be sent via Telegram chat. If a user tries to play the apparent video, he or she will receive a request to install a third-party app, which actually installs the malicious payload. Fortunately, the vulnerability has been resolved since July 11e2024, after we reported this to Telegram.
For questions about our research published on WeLiveSecurity, please contact us at threatintel@eset.comESET Research provides private APT intelligence reports and data feeds. If you have any questions about this service, please visit the website ESET Threat Intelligence page.
IoCs
A comprehensive list of Indicators of Compromise (IoCs) and examples can be found in our GitHub repository.
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
F159886DCF9021F41EAA |
Teating.apk |
Android/Spy.SpyMax.T |
EvilVideo payload. |
Network
|
I P |
Domain |
Hosting provider |
First seen |
Details |
|
183.83.172[.]232 |
infinitehackcharan. |
Beam cable system manager |
2024-07-16 |
C&C server of EvilVideo payload. |
MITER ATT&CK techniques
This table was built using version 15 of the MITER ATT&CK mobile techniques.
|
Tactics |
ID card |
Name |
Description |
|
Initial access |
Initial access exploitation |
The EvilVideo vulnerability can be exploited by Android malware to gain initial device access. |
|
|
Execution |
Exploitation for the execution of clients |
The EvilVideo vulnerability tricks the victim into installing a malicious app that mimics a multimedia file. |





















